Hello Everyone, I am a member of zh3r0 CTF team. We hosted our first CTF successfully. I hope you liked the CTF event. So, I made the 4 challenges in zh3r0 CTF. In which, 3 were forensics category and 1 was the web category.
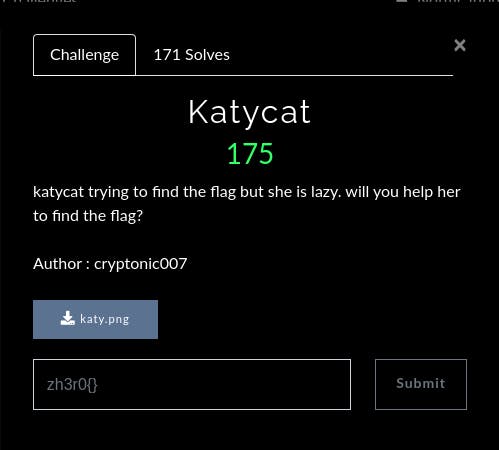
Katycat Challenge (Forensics)
katycat trying to find the flag but she is lazy. will you help her to find the flag?
Author: cryptonic007
First, download the png file. It is a png file. Let’s run the png stegano tools.
I run the zsteg tool and found a suspicious link.

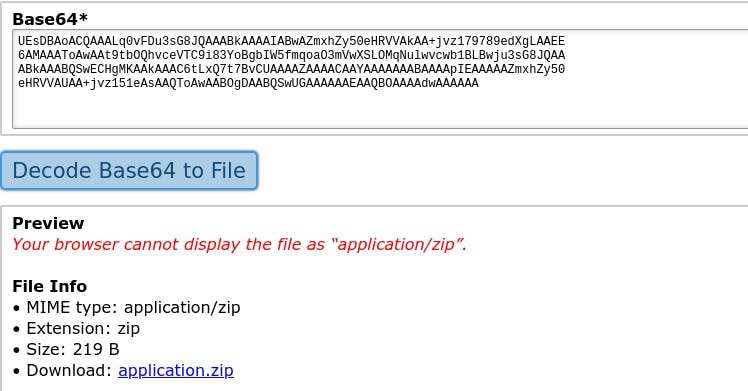
Let’s visit the link. I found something in base64.

Let’s convert into a zip file. I got the zip file. Download the zip file.
I tried to open the zip file but it was password protected. So, let’s find the password. I run the fcrackzip to find the password.

Open the zip using the password. We got the flag.txt. I opened the file and find some unreadable text, maybe it is encoded in something. Maybe, it is rot. Let’s figure out.
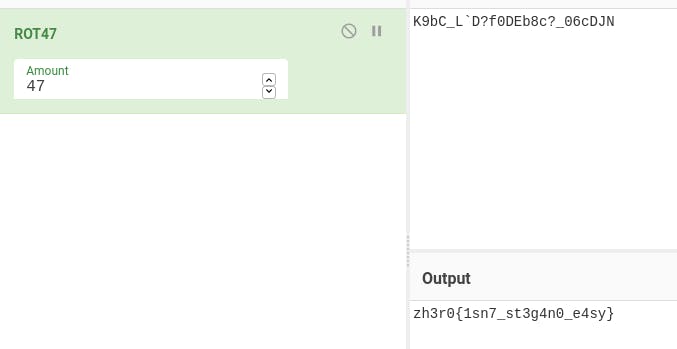
It’s rot47 and Boom…. we got the flag.
Flag: zh3r0{1sn7_st3g4n0_e4sy}
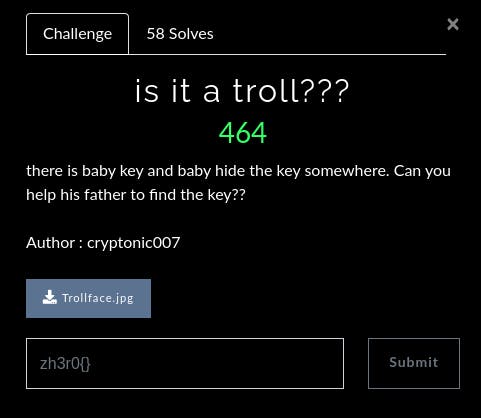
2. Is it a troll? (Forensics)
There is baby key and baby hide the key somewhere. Can you help his father to find the key??
Author: cryptonic007
First download the jpg file and try to find something worthy. So, I run Exiftool first to check what can I find.

In the author name, we found an encoded string. Let’s decode it.
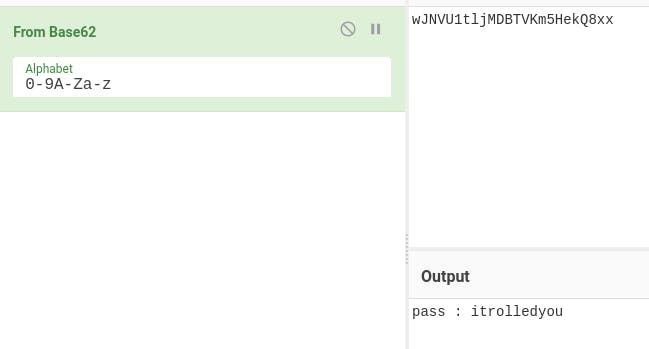
We got the password. There is maybe steghide tool used. Let’s try to extract the files.
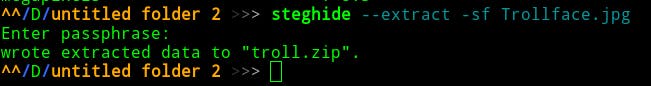
So, we got troll.zip. Let’s open it.
I extracted the zip and found one png file e.g troll.png. Let’s try to find something.
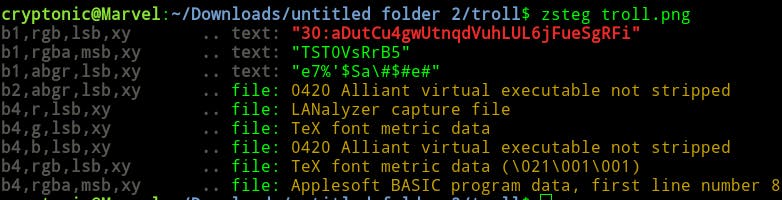
I found an encode string. Let’s decode it.

Hurray…..! We got the flag.
Flag: zh3ro{y0u_got_th3_k3y}
3. Find the the covid19 vaccine (Forensics)
There is vaccine located as flag somewhere. Find it
Author: cryptonic007

First, download the zip file. I extract the zip and found 30 jpg files and one pdf file. But, then Ilook carefully and saw that there is one png file between the jpg files. It was looking suspicious to me and I thought that something is there in a png file. I tried to find something. I run the stegsolve on a png file and got the password.

I checked and pdf was password protected. So, I opened the pdf using the password. In pdf, in the end, I found some weird text and they were looking suspicious. So, I start trying to get something from it.
Now copy the text and if you are not able to copy properly then use an online pdf viewer. Copy the text and paste then you will get the Unicode value. Decode the Unicode value and you will get the string.

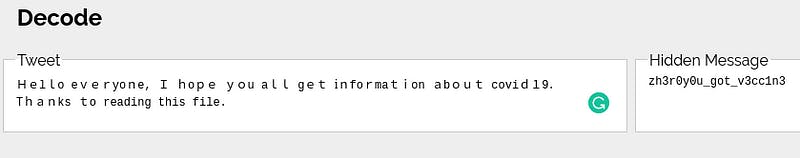
Boom…. You got the FLAG man.
Flag: zh3r0{y0u_g0t_v3cc1n3}
4. Fsociety (Web)
Chall Link: http://web.zh3r0.ml:6565/
I hate this society.Author : Cryptonic007,Finch
Automated tools allowed.
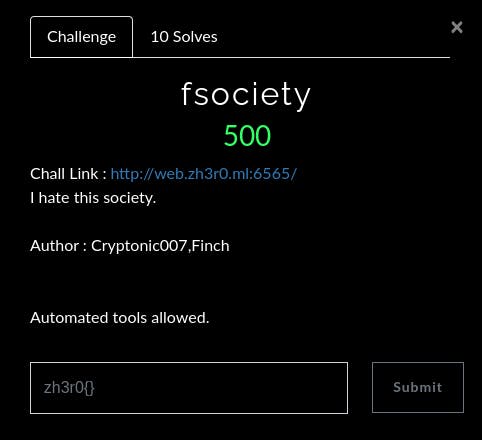
Open the given URL. You will find nothing. Now, check the robots.txt

We got the elliot.html. Let’s check elliot.html
Now check the source code of the file. we got the below image code.
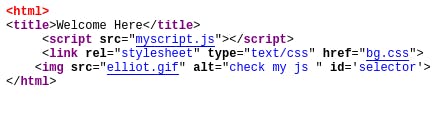
It’s saying check my js. There is js file. Let’s open it.
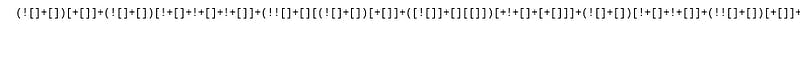
It is looking like jsfuck code. Let’s decode it.

We got something like fsocietyislit. Keep it in the note. Let’s run dir buster now.
I run the dirbuster. But, it was blocking and giving 503 error. So, I used Wfuzz and did the URL enumeration. I got this.
I opened the directory and got the flag.php file there. I opened the flag.php and got this.
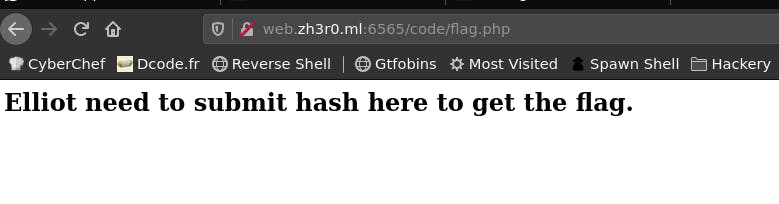
Means, we need to submit the code to get the flag. Maybe fsocietyislit is the code. Let’s try
I used the curl request to send the post request for code.
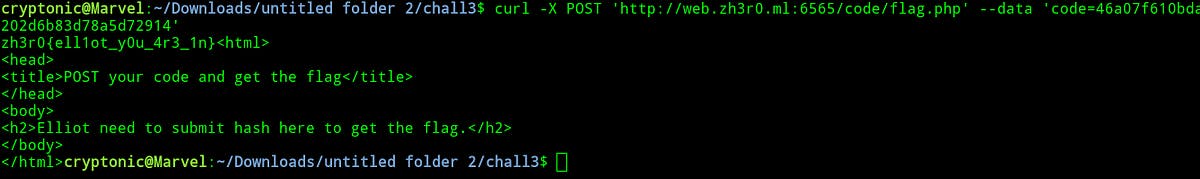
Boom…. We got the flag.
Flag: zh3r0{ell1ot_y0u_4r3_1n}
I hope that you all enjoyed the CTF. Thanks for playing the CTF.
You can follow me on Instagram and Twitter.
Twitter — mohitkchandani
Instagram — cryptonic007
