Hello All, we are back with part-2 of DEEP CTF. Let’s start with the writeup.
- Crypto Category
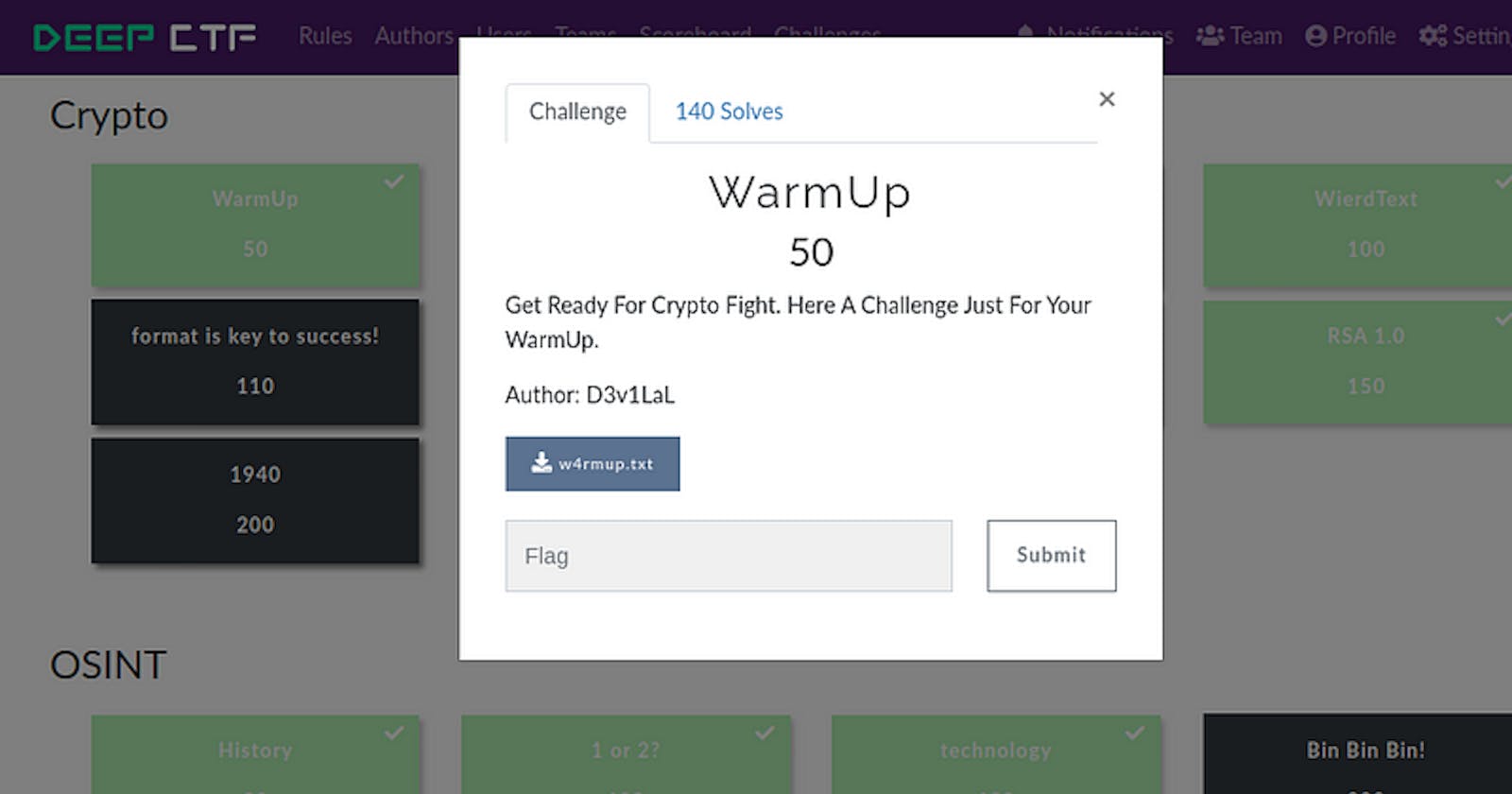
i) Challenge Name — WarmUp
Download the file and open it.

This file contains binary, decimal, hex, and octal encoding. So, decode them in parts and we will get the flag.
Flag: d33p{Ju5t_4_N0rm4l_Ch4ll__Isn`t_1t?}
ii) Challenge Name — WTf`ish

Download the file and see the text.

It is a brainfuck language. Let’s decode it.

Yeah. We got the flag.
iii) Challenge Name — Ali3nAgain
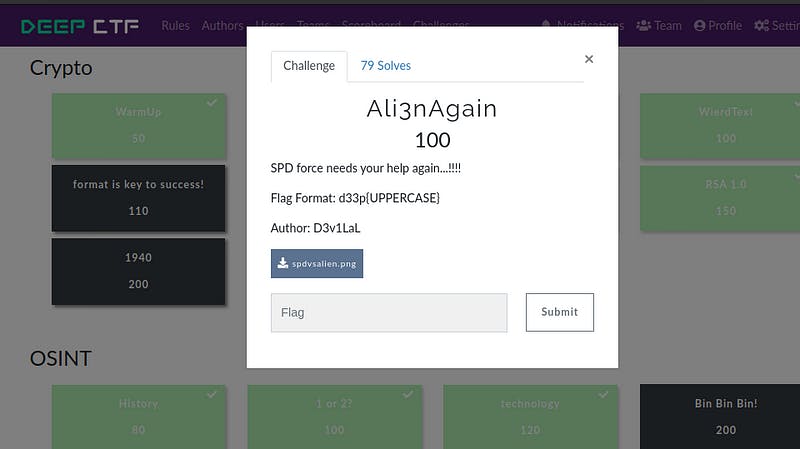
As they are saying in challenge alien again. I think, this file containing alien language. Let’s check it.

let’s decode it. Using this site http://cs.oswego.edu/~dreichel/alienese_decoder/. You will get the flag.
Flag: d33p{POWERRANGERSPDFORCEWON}
iv) Challenge Name — WierdText

Download the file and see the text.
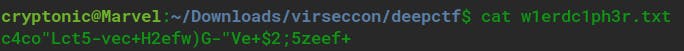
This is something weird text. But, they gave us a hint in the challenge that finds a new keyboard. Let’s find that there is any cipher related to the keyboard…OHH YES there is…Keyboard shift cipher.
Use it and decode it.
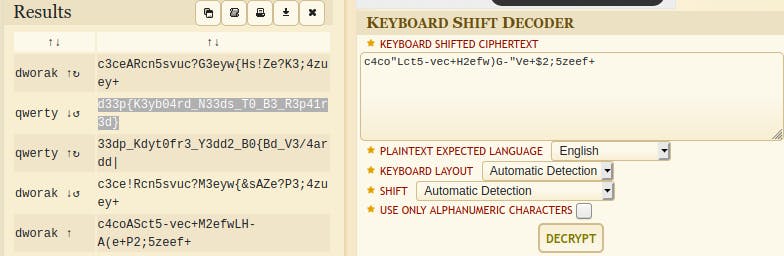
Voila…! You got the flag dude.
v) Challenge Name — Tr0ll
Download the file and check the text data.

It’s looking like base64. Let’s decode it.
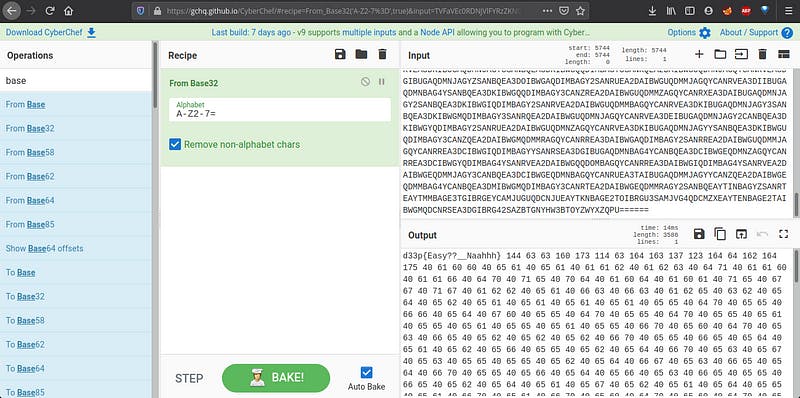
Ohh nice…Troll..fake flag..let’s decode again.
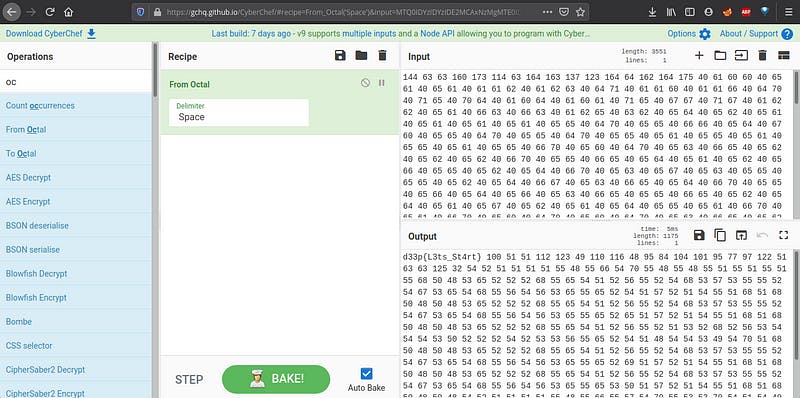
Again…Troll..It’s a decimal. Let’s decode it.
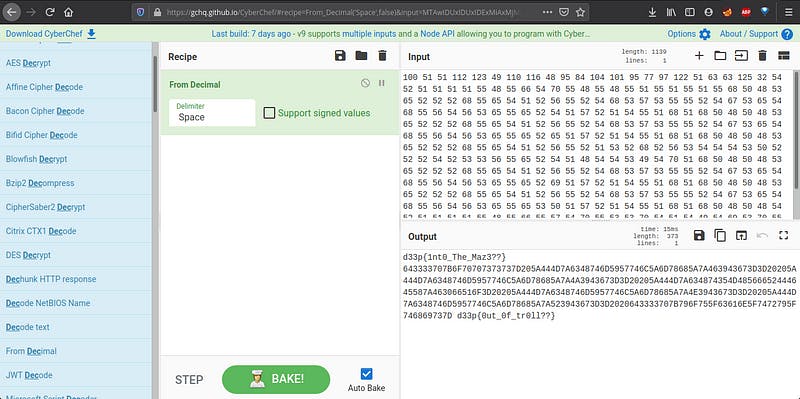
Let’s decode it again.
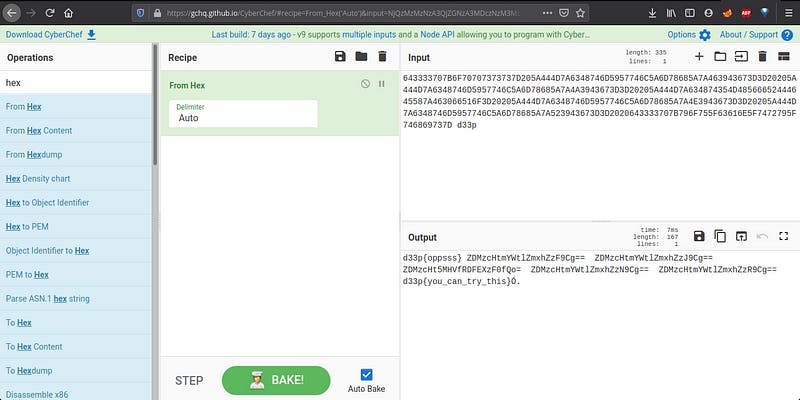
It’s a base64. Let’s decode it.

Finally…! We got the flag.
vi) Challenge Name — Ali3nCalling
Download the file and check the png file.

It’s looking like pigpen cipher. Let’s decode it.

Yeah. We got the flag easily.
vii) Challenge Name — RSA 1.0
Download the file and see the data of the file.
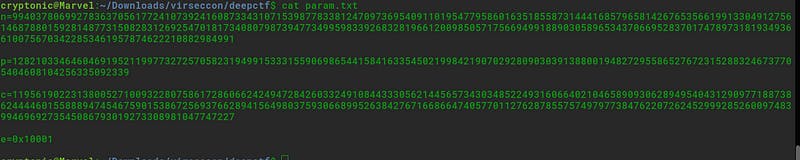
It is having all the parameters for RSA. Let’s use the RSA Tool to get the flag.
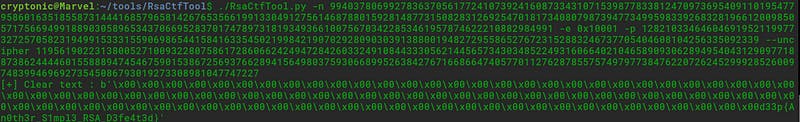
Cool. We got the flag easily again.
2. Misc Category
i) Challenge Name — Welcome
This one is an easy challenge. Just fill the google form and you will get the flag.
Flag:d33p{w3lc0m3_to_d33pctf0x01!!!!!!!}
ii) Challenge Name- Let’s chat!
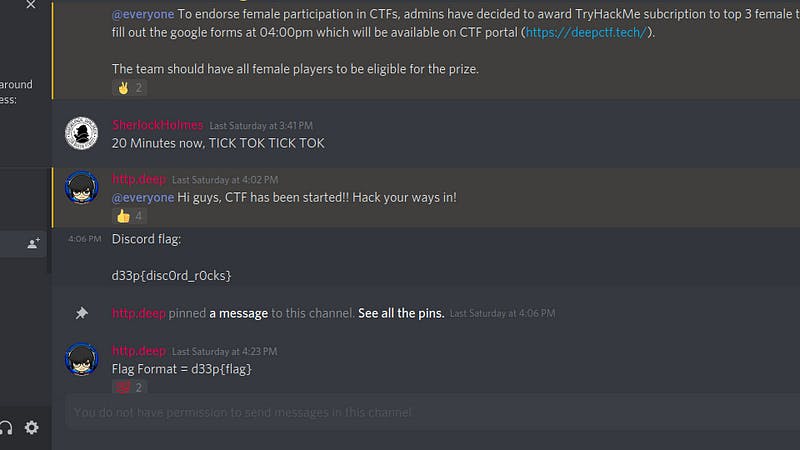
It’s simply saying to join the discord server. Join it and in announcements, you will get the flag.
iii) Challenge Name -Exploity Things
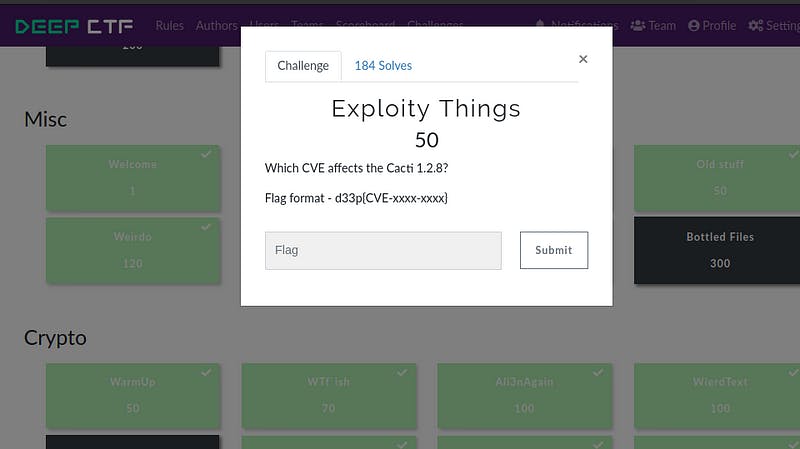
We have to just find the CVE for the given detail.
Google it.

Flag: d33p{CVE-2020-8813}
iv) Challenge Name — Old stuff

There is a paragraph that is saying the oldest way of hiding. Copy the text and google it.

Ohh… It’s Ceaser cipher. Yeah, It is one of the oldest techniques.
Flag: d33p{caesar}
v) Challenge Name — Weirdo

Download the file and see the text.
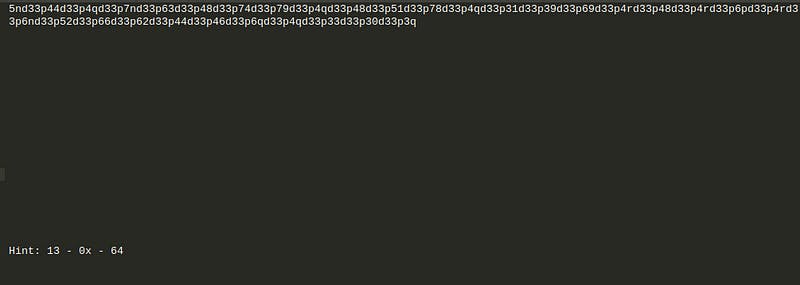
As we have hint 13–0x-64 means rot 13 →hex → base64.
Let’s decode it.

We got the hex. Let’s decode it.

We got the flag.
vi) Challenge Name — Should Have Used SSH.

Download the file.


We have extract files from capture, and we have 2 images :

Rename as a jpg file

I used stegcracker to brute-force passphrase.

Passphrase: murphy
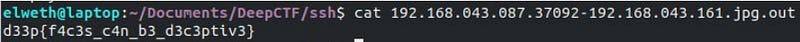
Flag: d33p{f4c3s_c4n_b3_d3c3ptiv3}
3. Web Category
i) Challenge Name-Oh JS!
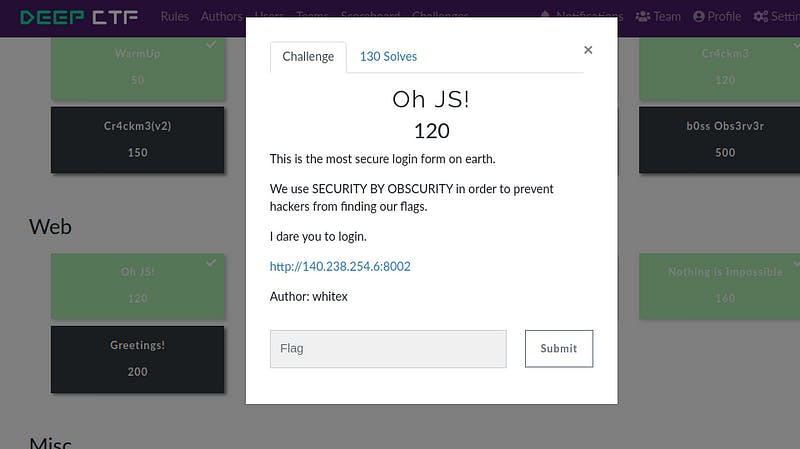
As challenge name says Oh JS!… means it’s related to javascript. Let’s check. Open the given URL. We got admin page. Now, check the source code. We find something…ohhhh.. that’s JS Fuck. Let’s decode it.

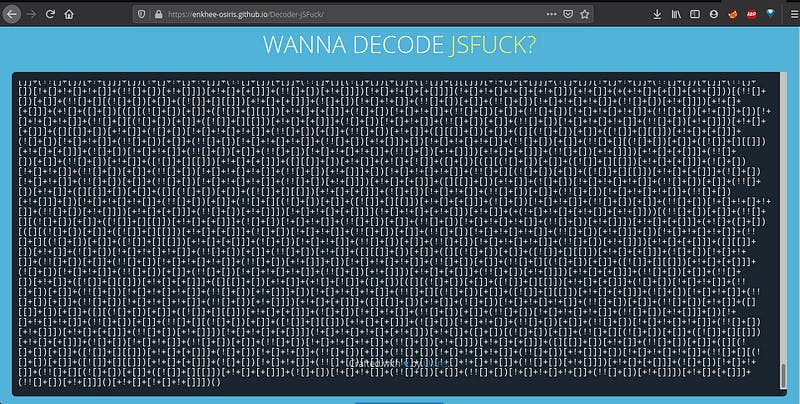
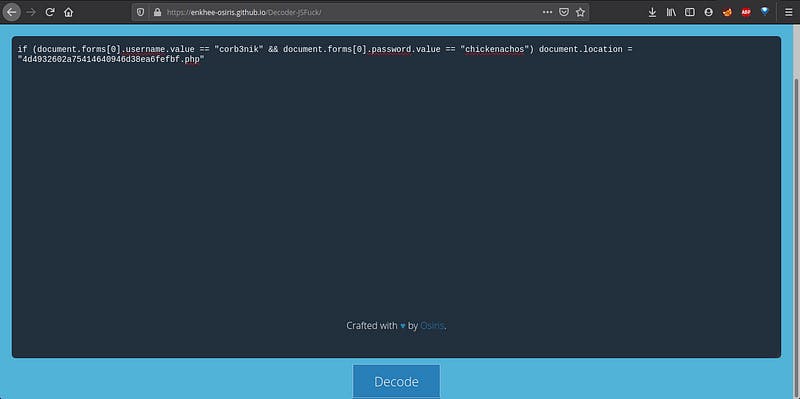
we got the admin username and password. Login through credentials. You will get the flag.
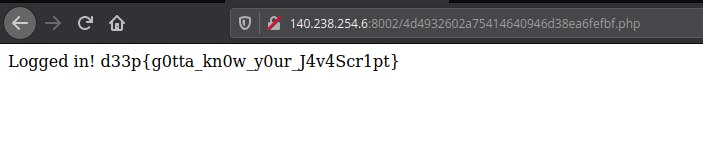
ii) Challenge Name — Magic Word!

Open the given URL.

Check the source code.

It’s removing the d33p and we have to magic_word=d33p to get the flag. Let’s change d33p with d33d33pp and submit.
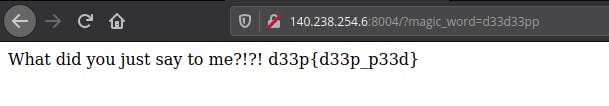
Yes…! We got the flag.
iii) Challenge Name — Nothing is Impossible
Open the URL.
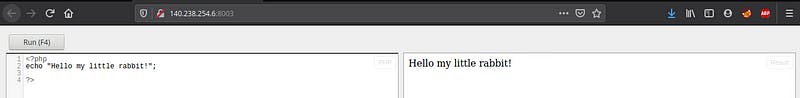
So, we are having PHP compiler here and as the description said that flag is located at /tmp/flag.php. Let’s get the flag.
flag.php had the a long output. So, I encoded that in base64.
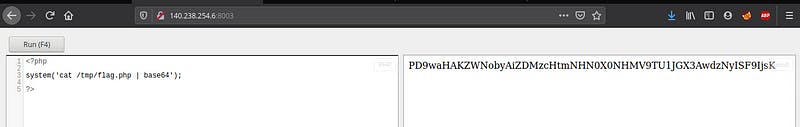
Let’s decode base64.
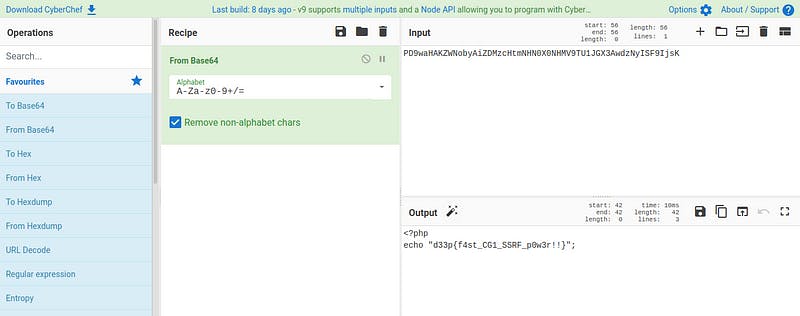
Yeah, finally we got the flag.
So, this was our DEEP CTF journey. I hope, you guys like this. I tried my best to make the writeup better as much as possible. If you have any suggestions or responses. You can put it in the comment box. That’s all my side guys. Bye.. We will meet soon with a new writeup. If you like, it just shares it.
Authors:
Cryptonic007 (http://instagram.com/cryptonic007)
[Login * Instagram
Welcome back to Instagram. Sign in to check out what your friends, family & interests have been capturing & sharing…instagram.com](http://instagram.com/cryptonic007 "instagram.com/cryptonic007")
DreyAnd (instagram.com/dreycoding)
[Login * Instagram
Welcome back to Instagram. Sign in to check out what your friends, family & interests have been capturing & sharing…instagram.com](http://instagram.com/dreycoding/ "instagram.com/dreycoding")
Elweth (https://twitter.com/Elweth_)
[Elweth
The latest Tweets from Elweth (@Elweth_): "First part of write up for @deepctf0x01 t.co/OGhaMf46eQ"twitter.com](https://twitter.com/Elweth "twitter.com/Elweth")