Hello Everyone, recently we participated in Deep CTF. We achieved 29th rank out of 477 teams. It was a jeopardy style CTF which includes OSINT, Crypto, Reverse, Web and Misc. It was a good experience for us and we learned new things in this CTF. Let’s start with the solution.
- OSINT Category:-
i). Challenge Name — History

Let’s just search “Drunk Hackers” up and find some location.

We find Location as defcon.org. Voila, we got the flag.
Flag: d33p{defcon}
ii). Challenge Name — Technology

Okay so we have an ASN(Autonomous System Number)which gives information about the victim‘s autonomous system, for instance: Registration date, maximal IP ranges, IP owner and other. Let’s try to do a quick lookup on it and see what we can find (Keep in mind that we are searching for a top product).
So I did a quick Shodan Lookup with ASN filter:


Flag: d33p{nginx}
iii). Challenge Name — Life
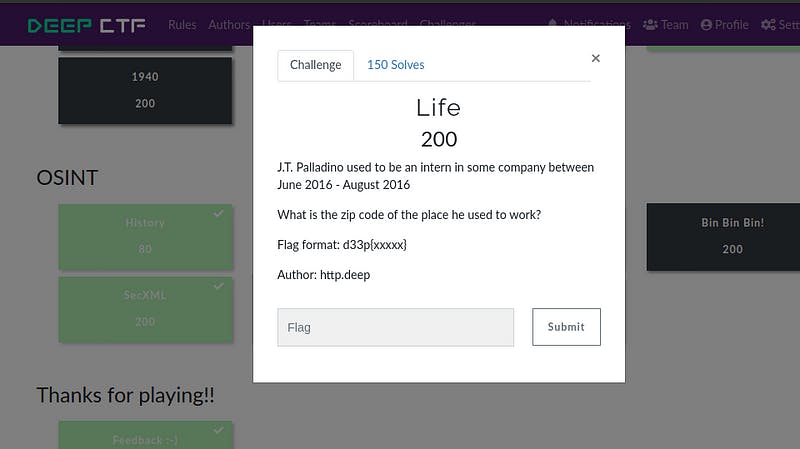
I searched up for J.T.Palladino up and found his LinkedIn profile which said that he was Data Quality as an intern from June 2016 — August 2016 - It Seems that it matches!
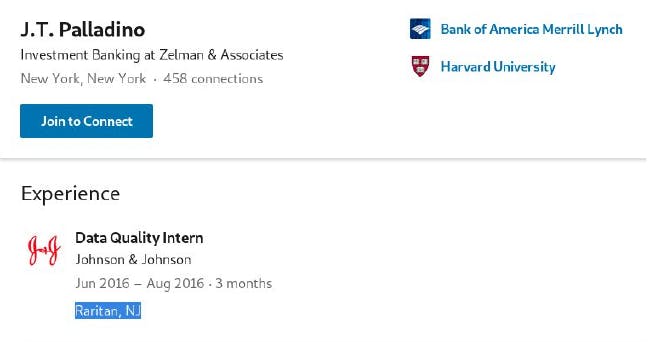
We see a location there — Raritan, NJ

Flag: d33p{08869}
iv). Challenge Name — Traveller
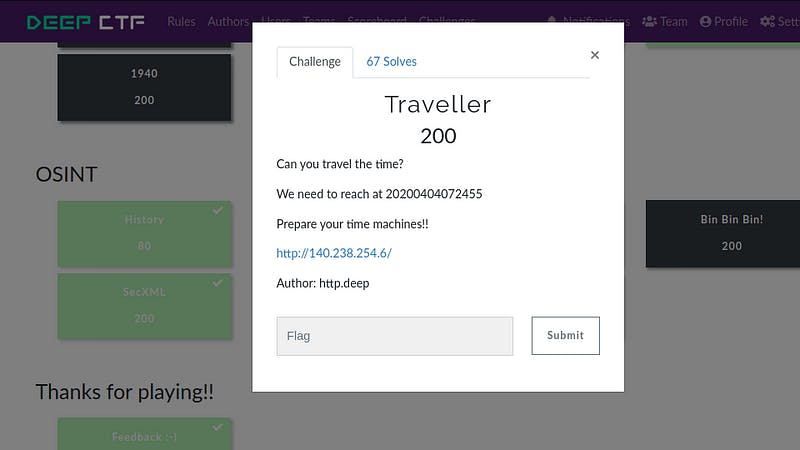
When I heard about travelling time. I knew what was going on here because I made a post on this on my Instagram profile([@dreycoding](twitter.com/dreycoding "Twitter profile for @dreycoding")). So we have to use archive.org. Archive.org(Also called The WayBack machine) is used to find snapshots of target websites before and after every change made by date. So we do have some date here(20200404072455), So let’s anatomize it to normal:
2020.04.04 07:24:55 - Now it’s understandable! Let’s open up archive.org.
Searching up just the IP doesn’t give anything related to this so I always the first search up some random well-known website.
For example https://facebook.com so I can, later on, use advanced
options to find what I need.

Let’s find our exact date:

Great! We have the flag -
ZDMzcHtjMG5ncjR0dWw0dGkwbiRfeTB1J3YzX3RyNHYzbGwzZF9iNGNrX3RpbUV9
But wait! It’s encoded! Let’s decode it as I assume that it is base64.
Flag: d33p{c0ngr4tul4ti0n$_y0u’v3_tr4v3ll3d_b4ck_timE}
v). Challenge Name — 1or 2?
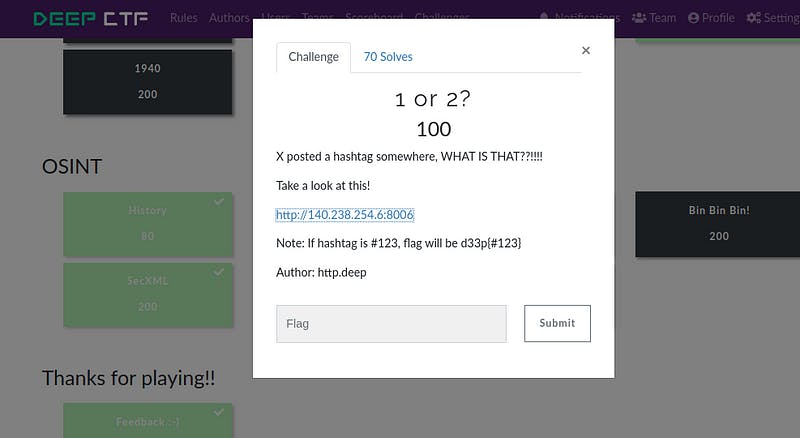
Open the given URL in the browser. You will find one corrupted image. Open the console and check the image name.


It is Image 2.jpg. When we try to open it, we got an error. Now, rename 2.jpg with 1.jpg and open it.
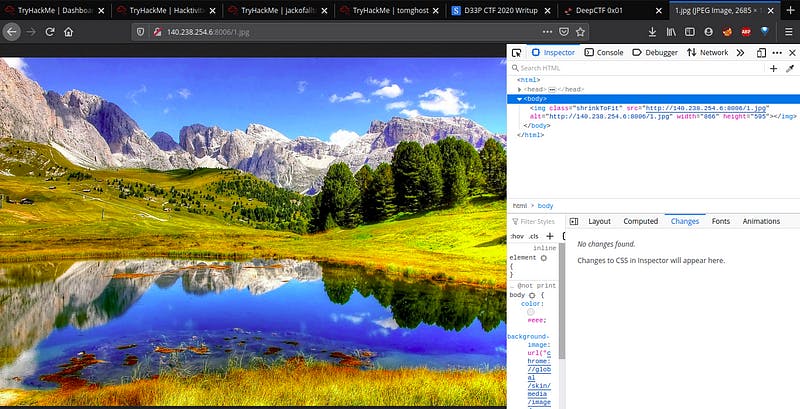
Download the image and use the Exiftool tool to analyze the image.
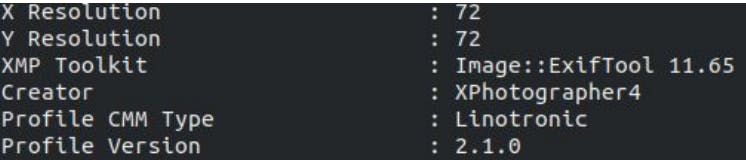
We got the creator’s name. Let’s search for it on google: XPhotographer4
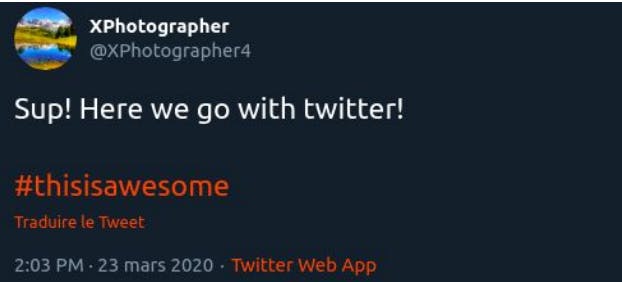
We found a twitter account with this name. When you visit the account, you will get the hashtag. Hurray..! we found the flag.
Flag: d33p{#thisisawesome}
vi). Challenge Name — SecXML
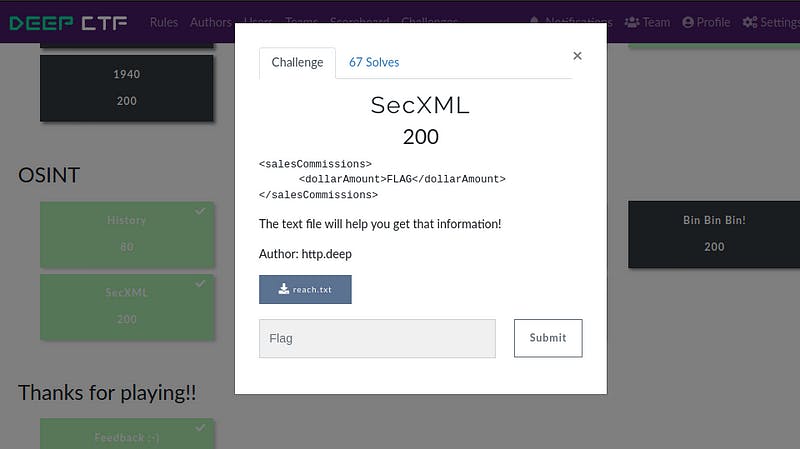
Download the reach.txt and you will find some text.
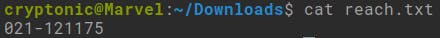
Google it. You will find some URLs. Check them

Find the dollar in these URLs.
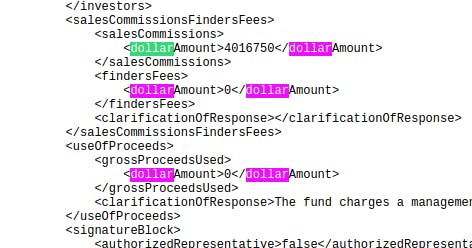
I think we got the flag. Yeah… we got the flag.
Flag: d33p{4016750}
2. Reverse Category
i) Challenge Name — Nested Rev

Open the given file using Ghidra Tool. It will list all the functions.

Find the main function.
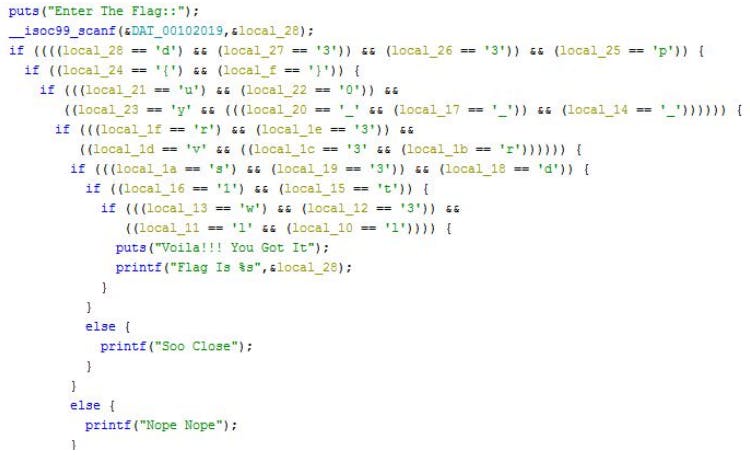
Just read the condition to get the flag.
Flag: d33p{y0u_r3v3rs3d_1t_w3ll}
ii) Challenge Name — SkipMe
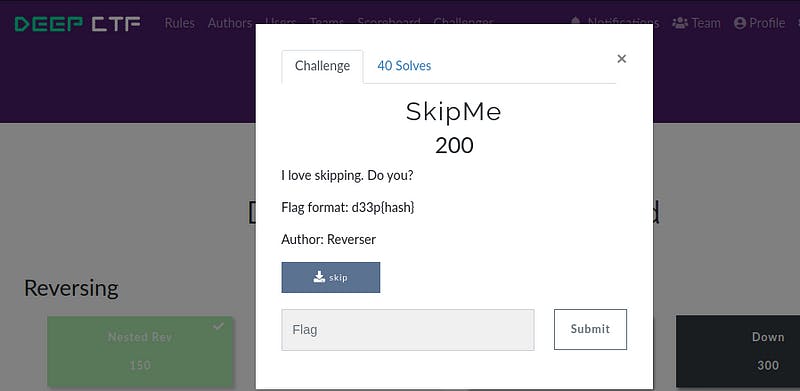
Open the given file with the help of gdb.

We discover the function finish which is called to print the flag, so let’s jump on this junction.
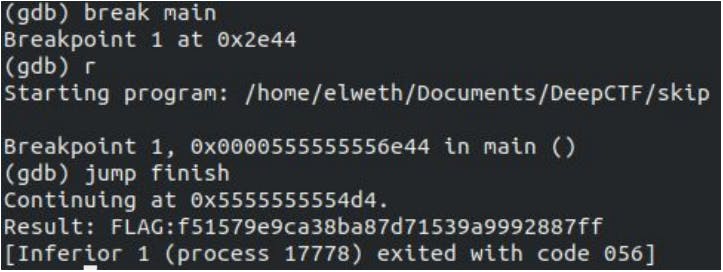
Flag : d33p{f51579e9ca38ba87d71539a9992887ff}
3. Forensics Category
i) Challenge Name — WarmUp

Download the jpg file. Let’s check the contains data in the image.


You will find the flag at the end of the jpeg file.
ii) Challenge Name — Find me
Download the jpeg file. As a challenge said that find the hidden things, So let’s try Steghide tool. Use the author’s name as the passphrase.

Hurray..! we got the flag.
Flag: d33p{st3gh1d3_1s_fUn}
iii) Challenge Name — MindYou

Download the zip file first and extract it. Zip files contain an corrupt image.
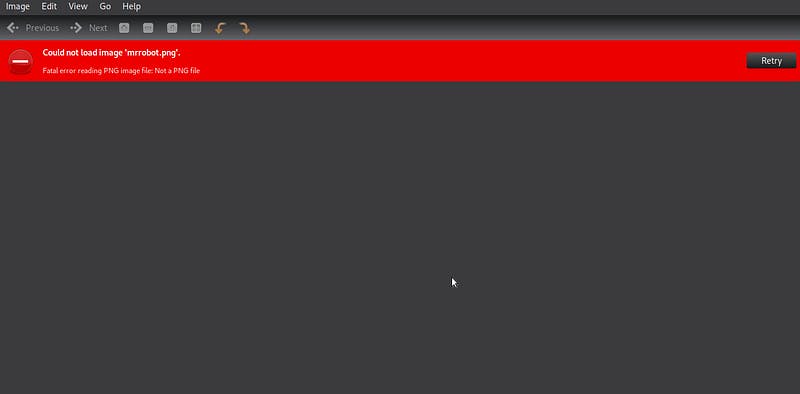
Let’s fix the image. Let’s check the header of the image file.
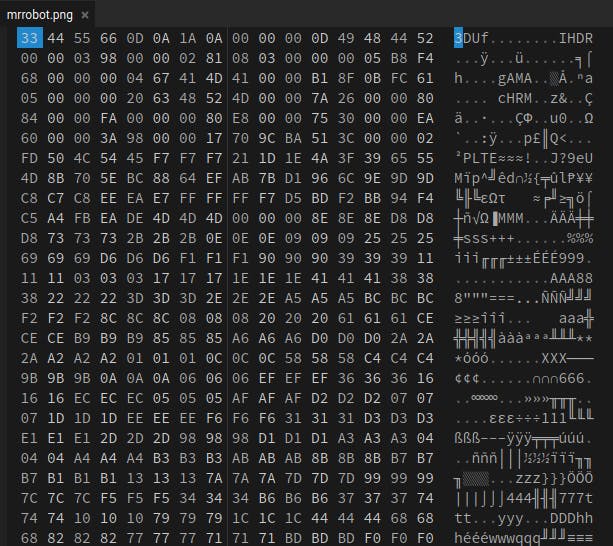
So the header is corrupt, fixes the header and tries to find the flag.

Hurray…! we got the flag.
iv) Challenge name — Cr4ckm3
In this challenge, we are having 2 files and both and password locked. So, we have to find the password.
So let’s grab the pdf hash using the pdf2john, save the hash in a file.hash and crack the hash using john the ripper tool.
#john — wordlist=~/Documents/dictionary.txt hashes.hash
password: melisateamo
Now, open the pdf. I see nothing special there but when I select all the text. I saw something weird.

I copied the text and paste in the sublime and I got the password.

Now, open flag.txt file using this password. Voila..! we got the flag.
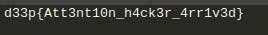
Flag: d33p{Att3nt10n_h4ck3r_4rr1v3d}
I think that writeup went too long. Hahaha… I don’t wanna make you sleep. This is PART -1. We will add more challenges in PART-2. Give your suggestions and response in the comment box. If you like it, just clap it. So, we will post more writeups in the future. Thanks to all for reading this writeup.
Authors:
Cryptonic007 (http://instagram.com/cryptonic007)
[Login * Instagram
Welcome back to Instagram. Sign in to check out what your friends, family & interests have been capturing & sharing…instagram.com](http://instagram.com/cryptonic007 "instagram.com/cryptonic007")
DreyAnd (instagram.com/dreycoding)
[Login * Instagram
Welcome back to Instagram. Sign in to check out what your friends, family & interests have been capturing & sharing…instagram.com](http://instagram.com/dreycoding/ "instagram.com/dreycoding")
Elweth (https://twitter.com/Elweth_)
[Elweth
The latest Tweets from Elweth (@Elweth_): "#HackTheBox #Multimaster Rooted! t.co/3F9Roo2TaF"twitter.com](https://twitter.com/Elweth "twitter.com/Elweth")