Hello Everyone, Let’s start with the writeup. So, There is a room on TryHackMe called CTF100 which is created by Deskel ( an amazing user of TryHackMe). This room contains total 100 flags, which are divided in different stages. Every stage have different methodologies , technologies and tools to get the flags. The themes of room is based on telent, cipher, encode and esolang. Let’s get started with solution.

Follow along with this writeup, and deploy your own instance of CTF100! https://tryhackme.com/room/ctf100
Task 1-1: Flag1
Start scanning the ip_address with the help of nmap.
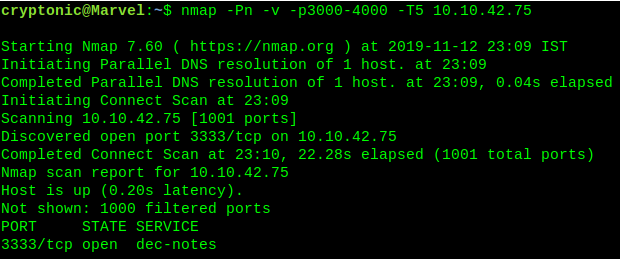
It is showing that port 3333 is open. Let’s dig on port 3333.
$ telnet <ip_address> 3333
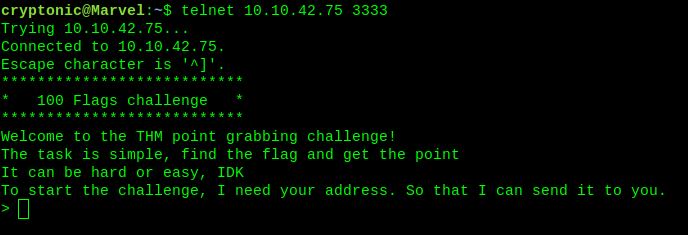
It will ask you for you address. Enter your address according to your tunnel ip.
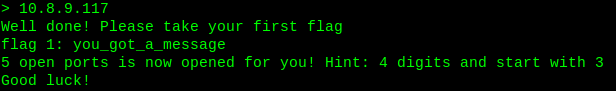
Woah.. We just get the first flag, and terminal also showing that 5 more ports are open now. Time to perform another scan using nmap.
Flag1: you_got_a_message
Task 1-2: Flag2
Do the nmap scan using below mention command.
$ nmap -v -T5 -p3000-4000 -Pn 10.10.42.75
So, we find the all 5 open ports. Let’s sart to dig on it.
$ telnet <ip_address> 3343
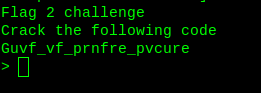
It is showing some enciphered text. Decipher text using ROT13.
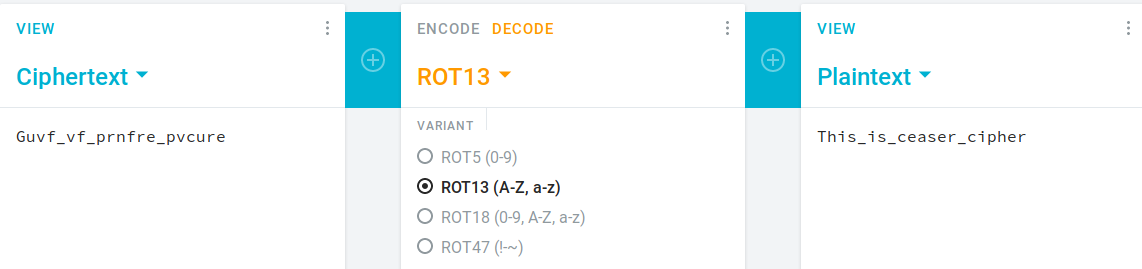
Enter the text to capture the flag and note the number, it will be use in upcoming steps.
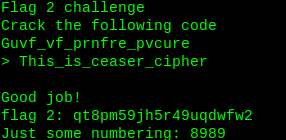
Flag2: qt8pm59jh5r49uqdwfw2
Task 1-3: Flag3
Let’s dig on next port.
$ telnet <ip_address> 3353
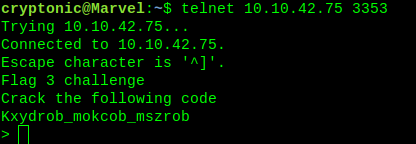
It is again a enciphered text. This is a ceaser cipher, decipher it.
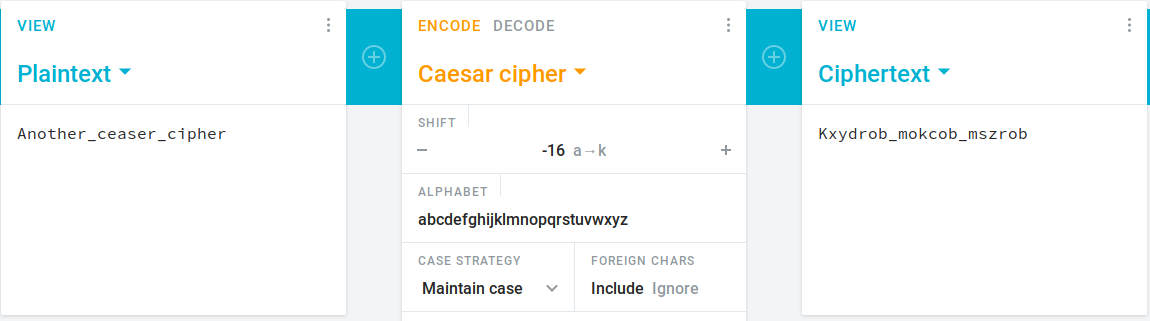
Keep rotating until you not get meaningful text.
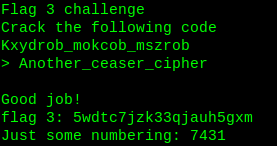
Flag3: 5wdtc7jzk33qjauh5gxm
Task 1-4: Flag4
Let’s check a new port for a new flag. Repeat the same telnet process but change the port number.
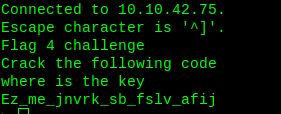
Now, where is the key?.. he is trying to make you fool bcoz key is where…hahaha
This is vignere cipher, decode it using the key and grab the flag.
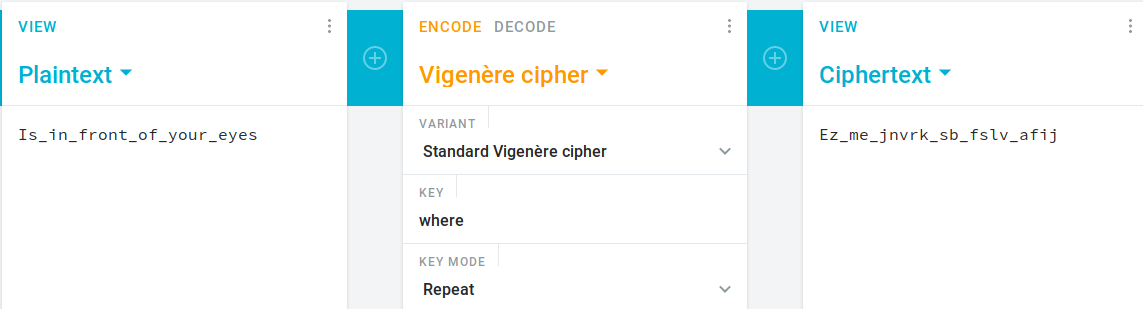
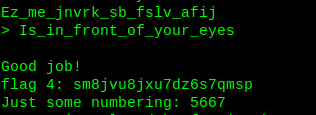
Flag4: sm8jvu8jxu7dz6s7qmsp
Task 1-5: Flag5
Next port.

It is morse code. Use a morse code translator to decode it and grab the flag.
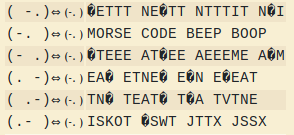

Flag5: 2p3363hrava9fbq296ca
Task 1-6: Flag6
Next port.
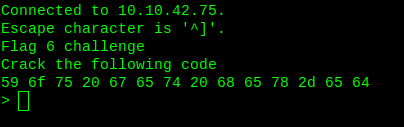
It is hex. Try to decode hex to ASCII.
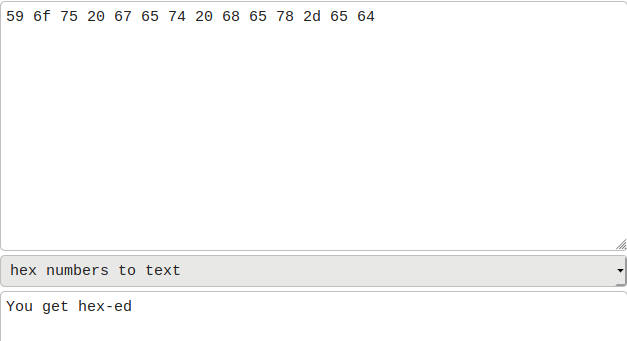
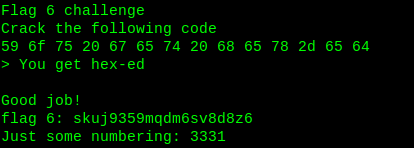
Flag6: skuj9359mqdm6sv8d8z6
Task 1-7: Flag7
Remember the number with each flag? Collected all 5 numbers are
8989 7431 5667 9332 3331
This sequence of these ports, open up port 9999. Enter these numbers on it.( The reason is port knocking)
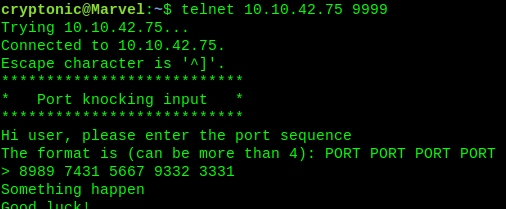
Something hapen… Time to perform a scan using nmap.
$ nmap -v -T5 -p4000-4999 -Pn <ip_address>

A new open port. Let’s check it.
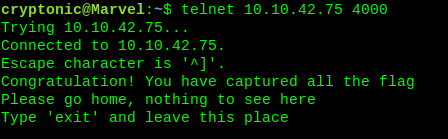
Do not trust anything it said. Maybe it is trying to fool you. Just press enter, it will show you something.
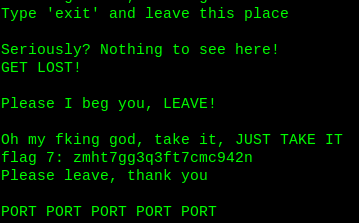
PORT PORT …. Means there are 5 more open ports. Time to scan again.
Flag7: zmht7gg3q3ft7cmc942n
Task 1-8: Flag8
$ nmap -v -Pn -T5 -p4000-4999 <ip_address>
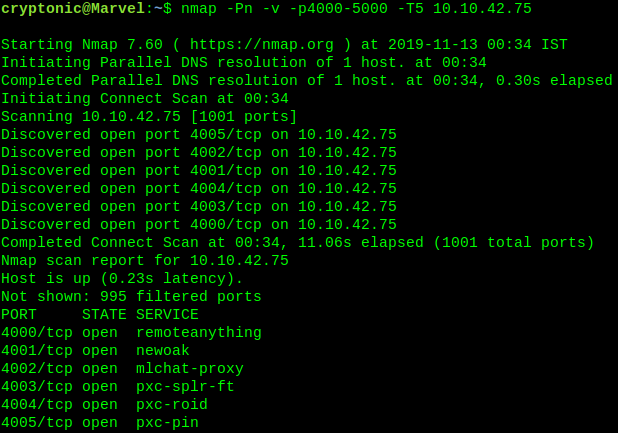
Let’s check on each port. 5 more challenges are ready to solve.
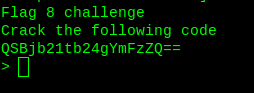
It is base64 text. Decode it.
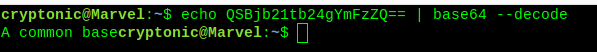
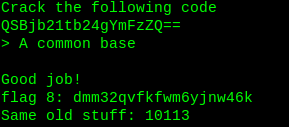
Save the number. It will be gonna help again.
Flag8: dmm32qvfkfwm6yjnw46k
Task 1-9: Flag9
Same Process. Check the next port.
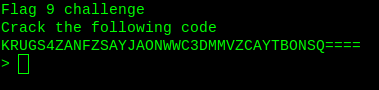
It is base32.
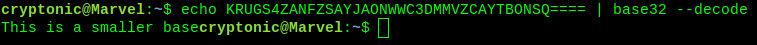
Flag9: fuf8mx74nph26f69mr97
Task 1-10: Flag10
Now, check port 4003. It seems like butter now ..right? Easy and simple… just go with flow and be ready for try harder level….hahhaha

This is base58 which is also look like base64. Decode base58
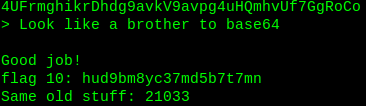
Flag10: hud9bm8yc37md5b7t7mn
Task 1-11: Flag11
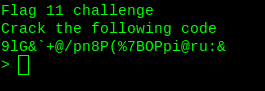
This is base85 looking like unreadable to us. Decode the base85.
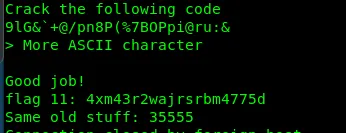
Flag11: 4xm43r2wajrsrbm4775d
Task 1-12: Flag12
port 4005… what do you have?
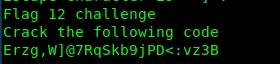
This is also unreadable and it is base91. Decode it.
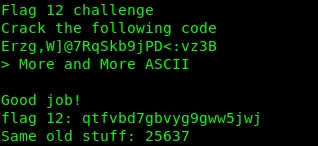
Flag12: qtfvbd7gbvyg9gww5jwj
Task 1-13: Flag13
Similar to Flag 1-7, collect all 5 numbers and open new ports using port knocking on port 9999.
According to flag, 5 numbers are
10113 10415 21033 35555 25637
But it is wrong sequence, reverse the order.
25637 35555 21033 10415 10113
Repeat same process, use port 9999 to open new ports.
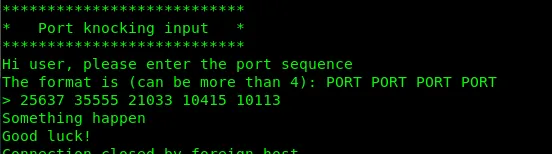
Something happen. Time to perform a new scan.
$ nmap -v -T5 -Pn -p-6000-6999 <ip_address>
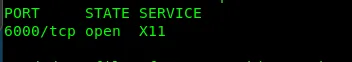
Voilaaa…. Port 6000 is open. Let’s check on this port.
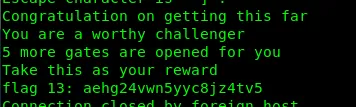
5 more open ports means 5 new flags…
Flag13: aehg24vwn5yyc8jz4tv5
Task 1-14: Flag14
Perform a new scan to identify 5 new ports.
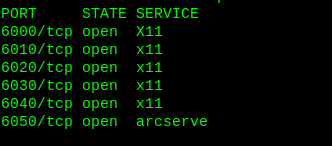
5 new open ports. Let’s dig on each one to find the flags.
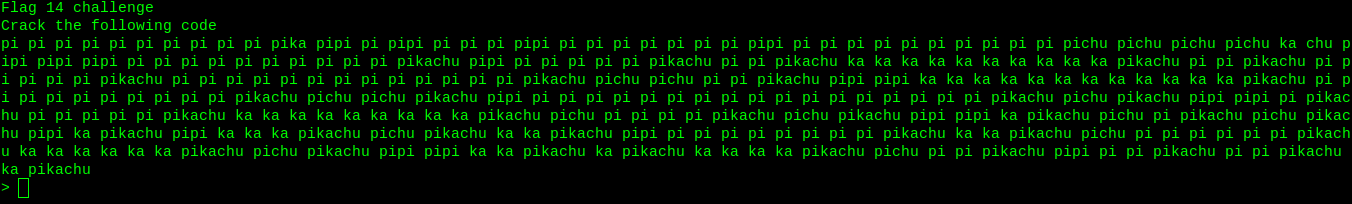
Remember something…sounds like pika pika pikachu…yes it is pikachu language. Actually, this is an esolang. Decode it.
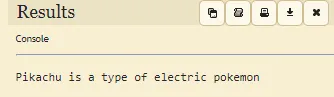

Flag14: k2phhw85emq3v4njj5g6
Task 1-15:Flag 15
Let’s check port 6020. What is it say?
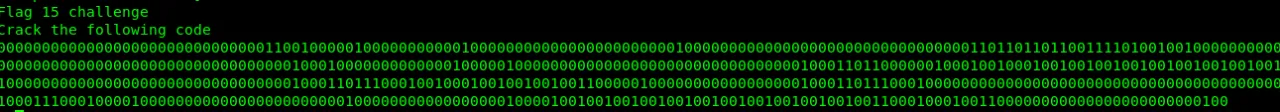
This is not simple binary language. This is another esolang which is binaryfuck. Let’s decode it.
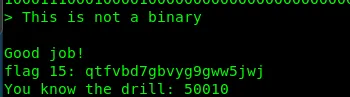
Flag15: qtfvbd7gbvyg9gww5jwj
Task 1-16: Flag16
Check port 6030…
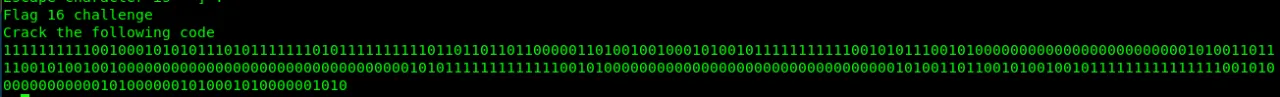
This is spoon esolang. Let’s decode it.

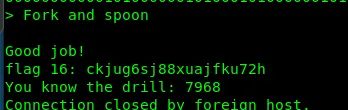
Flag16: ckjug6sj88xuajfku72h
Task 1-17: Flag17
Let’s check port 6040…
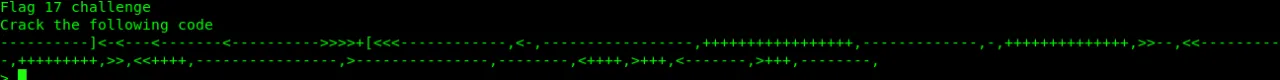
Looking like brainfuck…but is reversefuck language.
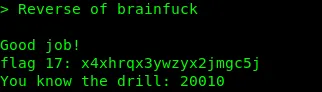
Flag17: x4xhrqx3ywzyx2jmgc5j
Task 1-18: Flag18
port port port hahhaha… it is last port to check 6050.(hope so xD)
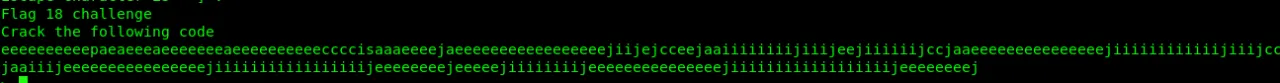
This is alphuck language.
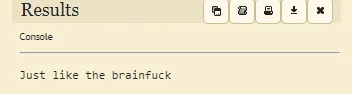
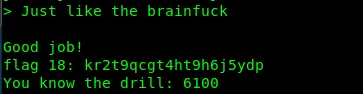
Flag18: kr2t9qcgt4ht9h6j5ydp
Task 1-19: Flag19
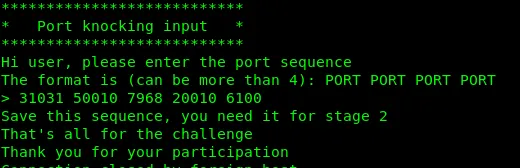
Collect all the 5 ports? yes…we did. This is port knocking for stage 2.
The sequence is
31031 50010 7968 20010 6100
Use these numbers to open ports in stage 2.
Ports: 31031 50010 7968 20010 6100
So, It was the writeup for stage1. For Stage2 and more, writeup will coming soon. Stay tuned and wait for writeups. Byee byee.

